Making and Unmaking Digital Wor(l)ds II
García — Milani
TODAY
Morning:
- Theoretical Iteration: Gamification and nudging
- Technical iteration: Network Infrastructure
- Practical iteration: Network Structure (Typologies)
Afternoon:
- Theoretical iteration: filter bubble
- Practical iteration: filter bubble and its discontents…
- Questions?
Quick Recap
- hacking is not only security hacking
- be aware of the «objective» and «objectal» dimensions of technical objects
- from sociometry to profiling
- interfaces
- tools > PAD https://go.circex.org/stgallen
Theoretical Iteration: Gamification & co.
Nudging Theory
Nudge theory 101

Nudge: Improving Decisions about Health, Wealth, and Happiness
- by economist Richard H. Thaler and Law School Professor Cass R. Sunstein, 2008
- The book draws on research in psychology and behavioral economics to defend libertarian paternalism and active engineering of choice architecture (not choosing for the others but influence the choice)
- influenced by Wiener (cybernetics), Kanheman & Tsverky (behavioural economics)
- example: the fly in the urinal
Genealogy of Nudging: Cybernetics And Behavioural Economics
- Cybernetics < ancient greek kubernetes (governor of the ship)
- Norbert Wiener defined cybernetics in 1948 as “the scientific study of control and communication in the animal and the machine.”
- Behavioural economics challenges the assumption that human rationality prevails.
- It asserts that humans’ actions are motivated and biased by a number of cognitive biases, such as “anchoring” (Kahneman, D., Slovic, P., & Tversky, A. 1982), the common tendency to rely too heavily on the first piece of information offered, called the “anchor”, when making decisions.
Gamification
- Gamification is “the use of game design elements in non-game contexts” (Deterding et al. 2011).
- The main purpose of gamification in digital worlds is:
- the creation of game-based incentives supposed to boost users’ engagement and retention on these platforms – and consequently in the processes they manage.
Genealogy Of Gamification: B. F. Skinner

Figure 1: Burrhus Frederic Skinner (1904—1990)
- psychologist, radical behaviourist: he considered free will as an illusion
- human actions depend on consequences of previous actions
- bad consequences > high chance of no repetition
- good consequences > high chance of repetition: reinforcement.
- the operant conditioning chamber, or Skinner Box
Operant Conditioning: We Are All Pigeons
- Operant conditioning (also called instrumental conditioning) is a learning process through which the strength of a behavior is modified by reinforcement or punishment.
- It is also a procedure that is used to bring about such learning.
Operant Conditioning Explained: Skinner’s Box Game
To Play The Game Of An Interface: A Pleasure That Generate An Addiction?
Circuits Of Pleasure, Circuits Of Pain The dopaminic system among repetition and behavioral reinforcement
Gamification or Digital Governance
The Game of the Interface and Us
- K., V., what are the interfaces-platforms-apps you use the most?
- the one you find more useful? (it can be the same)
- the one you consider more addictive (difficult to avoid, to interrupt while using)?
Our Interfaces-Platforms-Apps
- what are the interfaces-platforms-apps we use the most / we found more useful / addictive?
- everyone write down a list of three
- we share and we make a list of the most used / useful / addictive on https://go.circex.org/stgallen
Technical Iteration: Network Infrastructure
The Internet Quiz! How Does The Internet Works?
Question:
You Are In Europe And You Connect To (Deep)-Website (Facebook, Google Maps, Amazon.Com…). To Reach The Servers Of These Silicon Valley Companies, You Have To “Cross The Atlantic”. Internet Allows You To Do So But How?
1 - Geostationary Satellites?

Figure 2: Telstar I (First Communications Satellite Launched By Nasa On July 10, 1962)
Satellites in geostationary orbit. waves are bounced by satellites. There are fewer than fifteen thousand of them in orbit and new ones are continuously launched into space.
2 - Submarine Cables?

Submarine Cables, Which Since The Mid 1800s Have Been Laid On The Bottom Of The Oceans. At The Moment There Are Several Hundreds Of Thousands Of Km Of Cables.
3 - Radio Waves?
Radio Waves Of Various Types. Guglielmo Marconi Demonstrated At The Beginning Of The 1900s That It Was Possible To Communicate From One Side Of The Ocean To The Other. Radio Waves Today Are Much More Powerful — Wireless Technologies.
And The Correct Answer Is…
The Number 2. Cables!
cf. https://www.submarinecablemap.com/
But Why?
3 (Waves) No!
- Even If They Can Cross The Ocean, Radio Waves Are Too Dispersive (They Need To Be Framed).
- Above All, Radio Waves Do Not Transmit Enough Information
- Radio Waves Are Not Fast Enough.
1 (Satellites) No!
- Geostationary Satellites Are 36,000 Km From Earth
- We Communicate With Them Via Radio Waves (Same Problem), There Are No Wires That Connect Us To The Satellites.
- The Information Travels 72,000 Km…
- …While The Entire Circumference Of The Earth Is Just Over 40,000 Km, And The Atlantic Ocean Measures Less Than 5,000 Km At Its Widest Point.
2 (Cables) Ok!
- The Cables Are The Fastest Solution: Light Passes Through The Optical Fiber, Which Transmits Large Amounts Of Data At Very High Speed.
- On Earth, Other Underground Optical Fibre Cables And Wi-Fi Networks Are Used…
- …Such As Electromagnetic Waves With A Higher Frequency Than Radio Waves.
Video References
Practical Iteration: Network Structure
It’s Your Turn
Work Group.
- Explain (To Your Grandmother) The Differences Between Centralised And decentralised Digital Network (And How Can You Qualify Internet)
- Explain (To Your Grandmother) What Is A Protocol (And Give Some Examples)
- Explain (To Your Grandmother) The Differences Between Web And Internet (Give Some Examples)
- Explain (To Your Grandmother) The Differences Between Deep Web, Dark Web And Dark Net (Give Some Examples)
- Explain (To Your Grandmother) If It Is Possible To Remain Anonymous On Internet? How? Or Why Not? Give Some Examples.
- Explain (To Your Grandmother) what is an algorithm. Give some examples.
- Explain (To Your Grandmother) the concept of filter bubble.
Networks
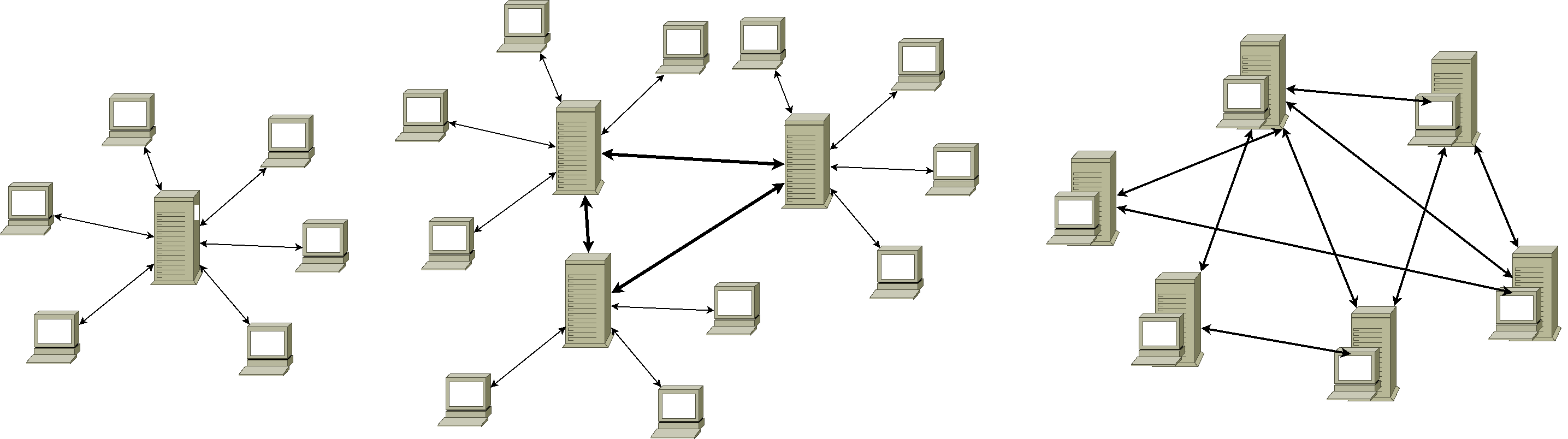
Figure 3: Centralized/decentralised/distibuted network
Internet
- Internet Is The Set Of Global Interconnections Active Over The Ip (Internet Protocol) Protocol
- Internet Is A Network Of Networks Much Larger Than The Web Alone.
Ip Protocols Not Web Related: Ftp, Imap, Pop3, Smtp (When You Send An Email Or Communicate Through A Client: Thunderbird, Filezilla…)
On Internet
… A machine needs to be identified.
An IP address identify the host (it is kind of a name given on the network)
And it provides the location of the host in the network, and thus the capability of establishing a path to that host (indicates the route).
It is a structural necessity to reach a computer, an object (IoT)
Protocols And Other Possible Agreements

- Machines Are Tuned To Each Other Via Protocols > Network
- Execute A Protocol = Negotiate An Agreement
- Handshake To Seal The Deal
- And If The Deal Doesn’t Work? → Bug. It’s The Normal State Of The Network!
Web
The world wide web is “an information space where documents and other web resources are identified by uniform resource locators (urls, such as https://www.example.com/), which may be interlinked by hypertext, and are accessible over the internet. The resources of the www may be accessed by users by a software application called a web browser.”
N.B.: Html Files On My Computer (E.G. These Slides) Are Not Part Of The Web, Although They Can Be Displayed With A Browser. // Google Examples
From The Web, Deep Into The Dark Web!
- Browsing The Dark Web (Easiest Method):
- Torbrowser
- Desktop https://www.torproject.org/download/
- Mobile tor browser android - orfox + orbot
- Many Services Are Accessible From .Onion Addresses
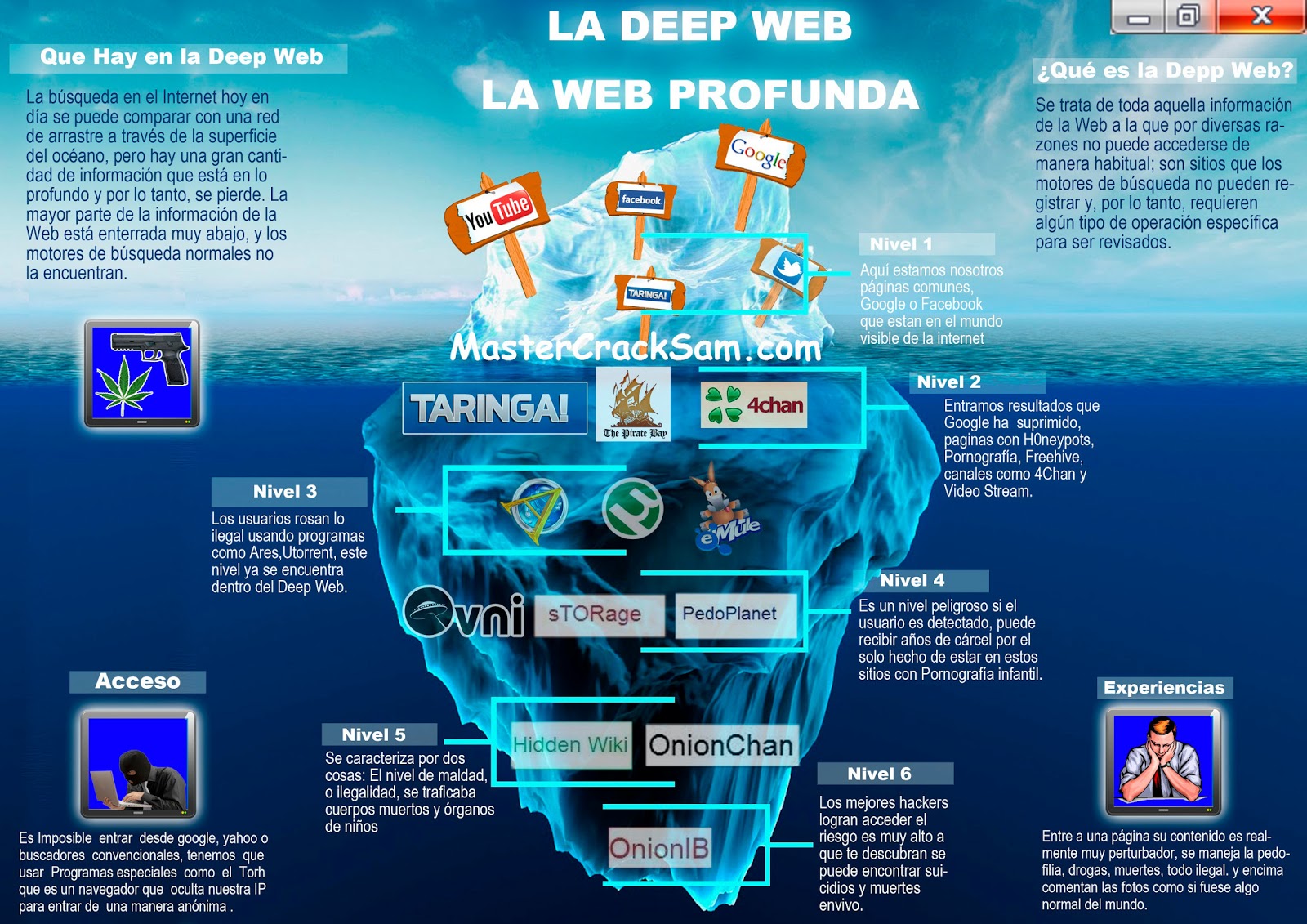
Deep Web
- We Call “Deep Web” The “”Parts Of The World Wide Web Whose Contents Are Not Indexed By Standard Web Search Engines. The Opposite Term To The Deep Web Is The Surface Web, Which Is Accessible To Anyone Using The Internet.“
- It Is Deep Because It Is Inaccessible To Any User. You Need To Know A Specific Access, Some Credentials, And/Or Interaction Capabilities.
- Http/S + Interaction = Deep Web // E.G. Sbb*
Dark Web
- The Dark Web Is That Small Part Of The Dark Net Accessible Through (With Ip Protocols Exposed Via Http/S) Specific Tools .
- The Best Known Example Is The Tor Web Networks, Accessible Via Tor Browser (For Example)
- But There Are Many More, Built On Other Systems Of Anonymisation Of Traffic And Users.
Dark Net
- “Dark Net” Is An Umbrella Term Describing The Portions Of The Internet Purposefully Not Open To Public View Or Hidden Networks Whose Architecture Is Superimposed On That Of The Internet (Ip Protocols, But Not Web, Http/S…)
- From A Technical Point Of View, A Dark Net Is A Type Of Virtual Private Network (Vpn) With Additional Measures To Obscure The Ip Addresses Of The Network Nodes.
- E.G. SSH - Whatsapp? - I2p
How To Take A Walk Into The Dark Web
- Download, Unzip, Click On Executable…
- And Go To One of The Most Commonly Used Site Of The Dark Web, Namely:
- onfothemostusedsiteofthedarkweb.onion
- A Dark Web Resource: hidden wiki
- Legal? Illegal? It Depends. Who Are You? Where Are You? What Are You Doing?
Typical “Terroristic” Representation Of The
Questions & Discussions
please mind the pad: https://go.circex.org/stgallen
Theoretical Iteration: Filter Bubble
Internet Wor(l)ds - The Game Of De-finitions
- Open the pad https://go.circex.org/stgallen
- Define: “Filter Bubble” (No Internet Help Allowed!)
Algorithms & Profiling
- First Example On Google: Ask For .Com And Get To .Ch Why? If/Then
- What Do You Do? > Research > Suggestions. Where Do They Come From?
- The Logic Of The Interface: Everything Is Explicit. Analysis.
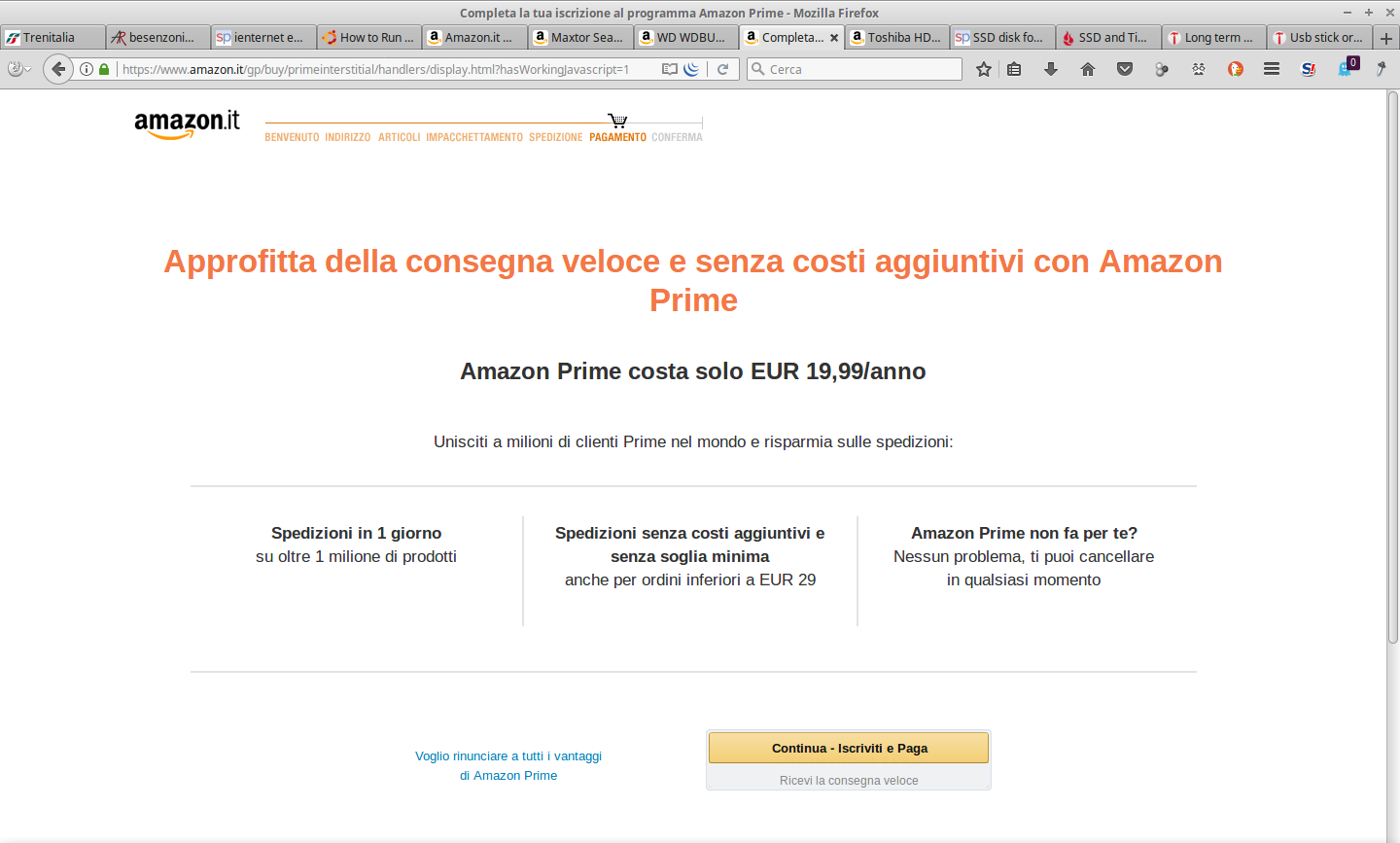
Amazon
- clean browser amazon > notice, notice: where are we?
- Go To Your Browser…
- Amazon From Torbrowser > Try Tor
- The Algorithm Criterion Through Interface Analysis: What Is The Rule? Is It Explicit/Implicit?
- Analysis: Proposals; Suggestions; Rankings
Practical Iteration - Filter Bubble
Power Browsing Tools
- see navigation on tor, analysis of ip on the two browsers
- pingtool
- downforwho
- geo traceroute
There’s Surveillance Everywhere…
“Surveillance is everywhere. Every digital interaction is monitored, recorded and stored” HOW TO DO?
feat. Bruce Schneier, “Data and Goliath”
- avoid
- block
- distort
- break
- see and show / educate
Avoid - I
Reason About The Tools, Change Your Behavior
- Cash, No Credit Card/Paypal/Cryptocurrencies
- No Social Account (At Least Not For The Children)
- No “Free” Web Services (Google Calendar, Webmail, Cloud)
- If You Do Not See The Price, You’re The Commodity…
- Don’t Install Software And Apps “For Free”!
Avoid - II
- Search with no-track engines: duckduckgo
- Do Not Discuss Sensitive Topics By Mail Or Messaging
- Write Messages By Hand, Photograph And Send
- Steganography…
Result: Customized Surveillance Remains; Automated Surveillance Is Much More Difficult And Expensive.
Block - I
Web Browsing (2021) - extensions
- ublockorigin ad blocker / lightweight / customizable / lpg 3.0
- privacybadger prevents tracking / learn from navigation / lpg 3.0
- noscript firefox to tor / activate scripts only on trusted domains / gpl 2.0
Block - II
- localization (smarthphone, gps, navigation)
- encryption: navigation (tor browser), email (pgp), data (cryptocat), password (keepassxc)
- computer webcam (scotch when you don’t use it, and if you know that the led does not work)
- glasses and other disguises anti-facial recognition dazzle
- say “no” > request data for advertising
Distort
- provide false data instead of rejecting it (addresses, names, etc.). anti anomaly detection
- let a bot click on everything (adnauseam)
- exchange accounts with friends for online purchases
- exchange loyalty cards / points
- container: firefox multi-account container
Break
- Play!
- Sometimes It Can Be Illegal… Take Care!
See - Show - Educate
*Surveillance Is In Place But You Can’t See It. Let’s Show It!
- where you come from country flags & ip whois
- what web app you interact with? wappalyzer
- read what you agree to! go easy, be careful, one thing at a time.
- everything stays! webarchive
- where have you been? lightbeam